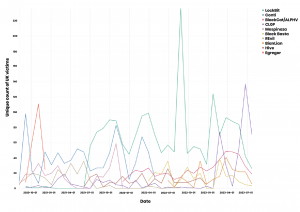
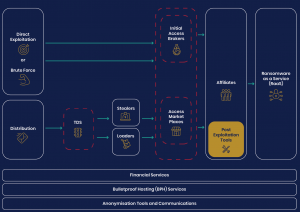
Related Posts
Bridging the Gap Between IT & Leadership: Communicating Cyber Risk to the Board
Bridging the Gap Between IT & Leadership: Communicating Cyber Risk to the Board We’ve all been there, technical teams talking in acronyms, execs focused...
Lessons Learnt from the British Library Cyber Attack
Lessons Learnt from the British Library Cyber Attack Whilst organisations must report any breaches to the ICO and inform impacted parties, there is still...
Retail Under Attack: How Layered Defence Reduces Cyber Risks
Retail Under Attack: How Layered Defence Reduces Cyber Risks Over the past few weeks, major retailers like M&S, Co-op, and Harrods have found themselves in...
Get in touch
SPEAK WITH AN EXPERT
01423 425 498
Related Posts
Bridging the Gap Between IT & Leadership: Communicating Cyber Risk to the Board
Bridging the Gap Between IT & Leadership: Communicating Cyber Risk to the Board We’ve all been there, technical teams talking in acronyms, execs focused...
Lessons Learnt from the British Library Cyber Attack
Lessons Learnt from the British Library Cyber Attack Whilst organisations must report any breaches to the ICO and inform impacted parties, there is still...
Retail Under Attack: How Layered Defence Reduces Cyber Risks
Retail Under Attack: How Layered Defence Reduces Cyber Risks Over the past few weeks, major retailers like M&S, Co-op, and Harrods have found themselves in...