Bridging the Gap Between IT and Leadership: Communicating Cyber Risk to the Board
We’ve all been there, technical teams talking in acronyms, execs focused on KPIs and somehow the real risks never make it to the right ears.....
"No Regrets"
Proactive Cyber
Assurance

Quantifying cyber risk

Strategic Security Planning

Reduced exposure and protected business value
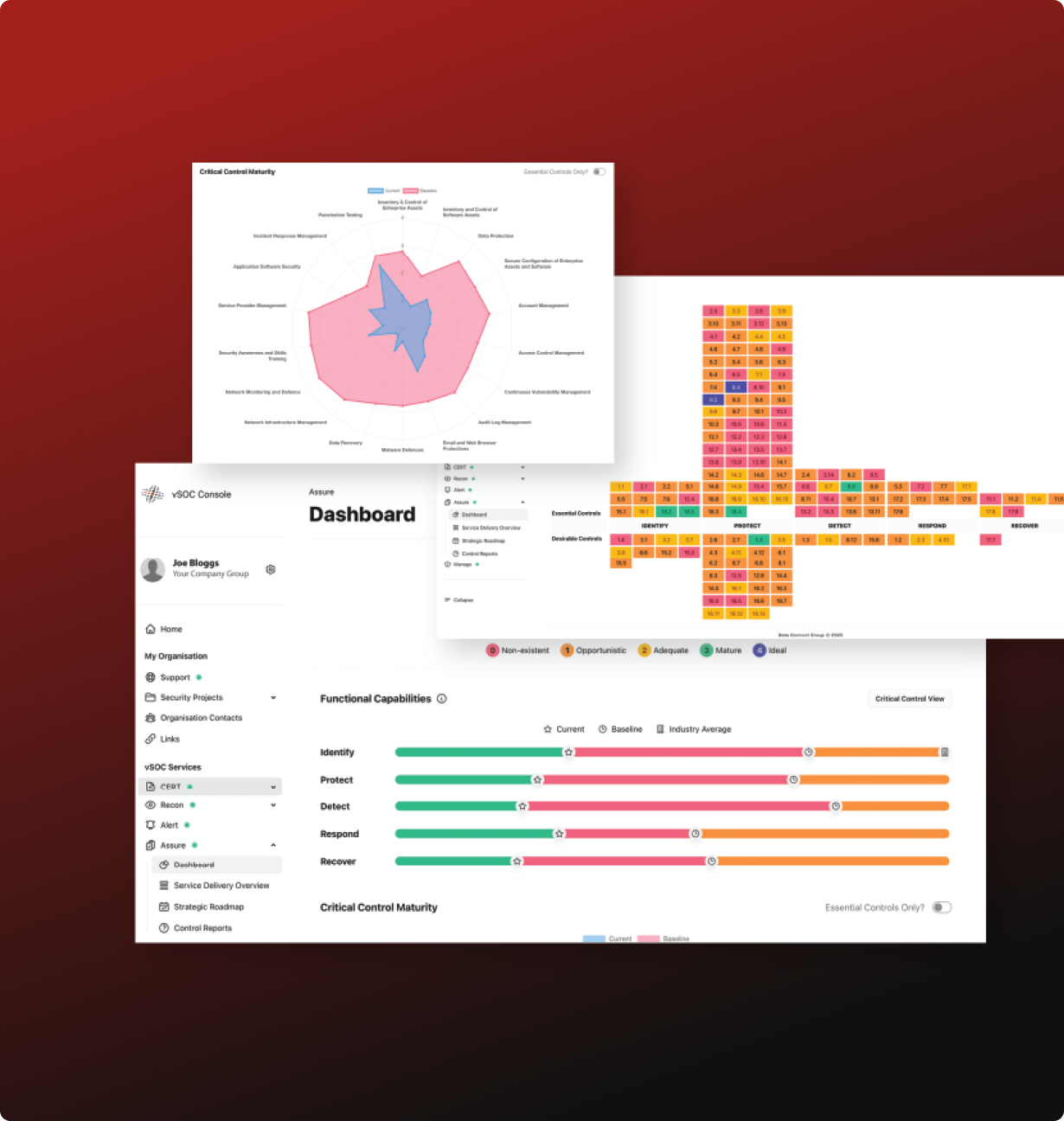
This powerful platform centralises all our managed services into one platform, providing you with actionable insights and access to powerful metrics, empowering informed decision-making.
> Executive Insight: Equip executives with a clear view of risk posture, performance and priorities giving decision-makers the context they need to lead with confidence.
> Management Tools: Using a combination of management tools, including Gantt charts, heatmaps and maturity matrices, we provide a comprehensive view of your risk posture.
> 360° Visibility: Experience seamless oversight of your cyber security services with full visibility and creating a clear, actionable security narrative from fragmented insights.

Have confidence that your security is in the right hands with the combined forces of our expertise, resources and knowledge.

Have confidence in your security. Cyber Essentials is a government-backed scheme that outlines the core technical controls an organisation needs to ensure an effective level of security. Through the support of our cyber experts and full visibility through the vSOC Connect Console, you can take the stress out of compliance and focus on building a secure and resilient organisation.

Government research found that 66% of organisations need to ask questions or seek help during their Cyber Essentials journey which is why we are proud to be a Certification Body, NCSC Assured Service Provider and Cyber Advisor. To achieve these, our security team and the business have been thoroughly assessed to confirm our deep technical knowledge, experience and outstanding customer service.

Verification from experienced security experts. Cyber Essentials Plus requires a technical audit to be completed, offering further assurances to not only you but your customers and partners. With 6 packages to choose from, Data Connect makes it easy to find the right fit, whatever your needs may be. You can identify vulnerability gaps, work through your compliance roadmap and even simplify recertification year after year with our platform.
Insights,
Trends and Advice


We’ve all been there, technical teams talking in acronyms, execs focused on KPIs and somehow the real risks never make it to the right ears.....


Whilst organisations must report any breaches to the ICO and inform impacted parties, there is still quite a lot of secrecy around individual cyber attacks....

The number of organisations achieving Cyber Essentials is growing each year. According to the NCSC Annual Review 2024.....

On the 2-3rd April, we spent two exciting days exhibiting at DTX Manchester....