Related Posts
Bridging the Gap Between IT & Leadership: Communicating Cyber Risk to the Board
Bridging the Gap Between IT & Leadership: Communicating Cyber Risk to the Board We’ve all been there, technical teams talking in acronyms, execs focused...
5 Key Takeaways From DTX Manchester 2025
5 Key Takeaways From DTX Manchester 2025 On the 2-3rd April, we spent two exciting days exhibiting at DTX Manchester. Lots of interesting talks...
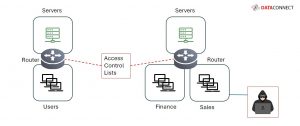
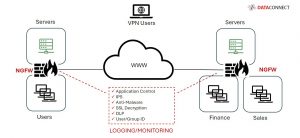
Identifying and Fixing Common Firewall Misconfigurations
Identifying and Fixing Common Firewall Misconfigurations The role of the firewall has shifted a great deal in the last decade, becoming more and more feature...
Get in touch
SPEAK WITH AN EXPERT
01423 425 498
Related Posts
Bridging the Gap Between IT & Leadership: Communicating Cyber Risk to the Board
Bridging the Gap Between IT & Leadership: Communicating Cyber Risk to the Board We’ve all been there, technical teams talking in acronyms, execs focused...
5 Key Takeaways From DTX Manchester 2025
5 Key Takeaways From DTX Manchester 2025 On the 2-3rd April, we spent two exciting days exhibiting at DTX Manchester. Lots of interesting talks...
Identifying and Fixing Common Firewall Misconfigurations
Identifying and Fixing Common Firewall Misconfigurations The role of the firewall has shifted a great deal in the last decade, becoming more and more feature...