
Whilst organisations must report any breaches to the ICO and inform impacted parties, there is still quite a lot of secrecy around individual cyber attacks. A refreshing take though, by the British Library, was how they released a report last year highlighting the full extent of the attack that caused chaos in 2023. Included in this report was a look into the attack, its impact, the crisis response and recovery stage and lessons learnt by the institute. They released this document in order to help their peers and the wider business community, so they don’t make the same mistakes.
This blog will explore this fascinating case study, with our very own take on the situation as cyber security experts.
Cyber Attack Background
On Saturday 28th October 2023 the British Library suffered a significant cyber attack which involved ransomware that compromised the majority of the library’s online systems.
Their data was stolen and encrypted, with the criminal gang responsible for the attack copying and illegally removing over 600GB of files, including personal data of library users and staff. The ransomware gang who claimed the attack was Rhysida, a group which arrived on the scene early in 2023 and are motivated specifically for financial gain. In the attack, the malicious actors also encrypted and destroyed significant parts of their server estate, locking out network users.
Here is a quote from the report, detailing the morning’s actions following the breach identification:
“The intrusion was first identified as a major incident at 07:35 on 28 October 2023 when a member of the Technology Team was unable to access the Library’s network. Initial escalation and investigation of the incident within the Technology Team as per the Technology Major Incident Management Plan confirmed the likelihood that the incident was the result of a cyber-attack; and at 09:15 the Library’s Crisis Management Plan was invoked by the Business Continuity Manager. The Accounting Officer and Chief Officers were contacted and informed of the incident by 09:21 and the Gold Crisis Response Team subsequently notified, convening at 10:00 by WhatsApp video call in the absence of email”
UK Government entities are restricted from paying ransoms, which meant that the British Library didn’t communicate or pay the ransom. Once it was evident that no ransom would be paid, the data was listed for auction and released on the dark web. The starting bid on Rhysida’s leak site was of 20 bitcoin, or about £590,000.
The Impact of the Cyber Attack
The impact on services was deep and extensive! With systems literally destroyed beyond use and services impacted for months. Most damaging to the operations of the British library was how they simply couldn’t recover. Many of the systems they used were so old they couldn’t be rebuilt as the software wasn’t available or it didn’t make sense to rebuild old vulnerable systems.
The Library’s complex technology estate, stems from its origins as a merger of various collections and functions. The complexity and legacy infrastructure is believed to be the reason for the severity of the attack. It provided attackers with broader access than a modern network design would permit, and the dependence on older applications using manual processes to transfer data between systems led to an increase in the volume of staff and customer data stored in multiple copies across the network.
The effect on the Library’s systems and services has been significant and far-reaching. Whilst the Library premises stayed open, (including exhibitions, events, and Reading Room access), research services faced severe limitations during the initial two months and continued to be incomplete, even after the searchable version of the online catalogue was reinstated back in January 2024.
Incidence Response and Recovery Following the Cyber Attack
Following the attack, they performed the following tasks:
- They didn’t pay the ransom
- Notified relevant parties including – those with compromised data, key stakeholders, staff, other users of the systems.
- Purchased Credit Monitoring and Identity Protection – for staff, including ex staff and others to protect their personal finances.
- Brought in Forensic Analysists
- Started a Rebuild and Renew Program.
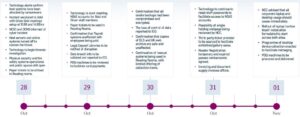
It is strongly believed by the forensic investigators that the malicious actors had gained access initially at least three days prior to the incident being identified. The British Library and its advisors believe this initial breach to have been a hostile reconnaissance of their network, serving as a precursor to the attack.
“The most likely source of the attack is therefore the compromise of privileged account credentials, possibly via a phishing or spear-phishing attack or a brute force attack where passwords are repeatedly tried against a user’s account.”
By December 2023, the British Library was ready to shift between crisis response to recovery, with the introduction of a Rebuild & Renew programme. This initiative seeks to restore services and revamp their technological infrastructure, creating a more secure and innovative British Library. It integrated with ongoing modernisation efforts, but at an accelerated rate.
“Due to the complexity of restoring, modifying, consolidating, retiring, rebuilding or replacing a large number of systems at the same time there will need to be a careful balance of informed analysis, visionary design, and firm objective setting and management.”
Key Takeaways From This Cyber Attack
So, the big question is, what can WE all learn from this attack?
In the original report, the British Library highlights 16 lessons that they’ve taken away from this situation and what they believe could help other people. For many organisations, it’s often hard to know where to start and can be quite overwhelming. To reduce this, one of Data Connect’s security experts have analysed the lessons, reducing the list down to 4 core messages.
- Taking Security Seriously – They underestimated their appeal as a high-value target and now see cyber security as something that must be key to their IT strategy.
- Future risk assessment must appreciate risk – This tells us that they didn’t truly understand the risks they faced. The Library did a good job of escalating serious security risks that required urgent action. However, it wasn’t as effective at tracking and understanding how many smaller, low-level risks were present overall. These smaller risks might not seem concerning individually, but when considered together, they could add up to a bigger issue.Management needs to be aware of both major and minor risks so they can make informed decisions about cyber security.
- Lessons from disruption – They will look to ensure that they are more resilient to disruption and have recovery capabilities. Here are some methods mentioned by the British Library: the importance of practicing their comprehensive business continuity plans, checking on staff wellbeing post attack and, how security and recovery must go hand in hand.
- Prioritised Measures – In their own words, “the security measures they had in place on 28 October 2023 were extensive and had been accredited and stress-tested, however with the benefit of hindsight there was much they wished they had understood better or had prioritised differently”.
The British Library had established cyber security measures, but the cyber attack revealed areas where their approach could have been a lot stronger. While they had protections in place, they hadn’t fully recognised the extent of the risks they faced or prioritised security measures as effectively as they now wish they had. Like many organisations, they followed established cyber security practices, but this incident highlighted the need for a deeper, more proactive approach.
How to Move Forward
The British Library’s experience serves as a valuable lesson in cyber security. More than just technical defences, organisations need a real understanding and a strategic approach to protecting their systems. Simply following routine security practices isn’t enough, sophisticated threats require proactive risk management and continuous adaptation.
Cyber security isn’t just an IT issue; it’s a leadership priority. Organisations must take security seriously, assess risks with honesty, and ensure they have the resilience to recover when incidents occur. Many of the lessons learned from this attack revolve around risk—effectively managing cyber risk is not optional, but essential for long-term security and stability.
Whilst the British Library had the resources and funds to recover after the attack, many organisations are not this fortunate.
Watch our on-demand webinar “What the Real-World Attacker Thinks to Your “Real-World” Approach to Cyber Risk” here.
In this webinar we cover:
- Gain a deeper understanding of the real-world impact of cyber incidents
- Bridge the gap between theoretical threats and the actual risks your organisation face
- Discover the real value of compliance and pen testing
- Learn about the common pitfalls of traditional security methods
- Explore the importance of visibility in cyber security
- Find a more effective approach to risk that aligns with your business objectives
Want to discuss your current risk exposure and how to overcome security gaps with our experts?
Get in touch or explore our vSOC Assure service to learn more about navigating your organisation’s cyber risk with a trusted security partner.

