vSOC Recon
Attack Surface Management
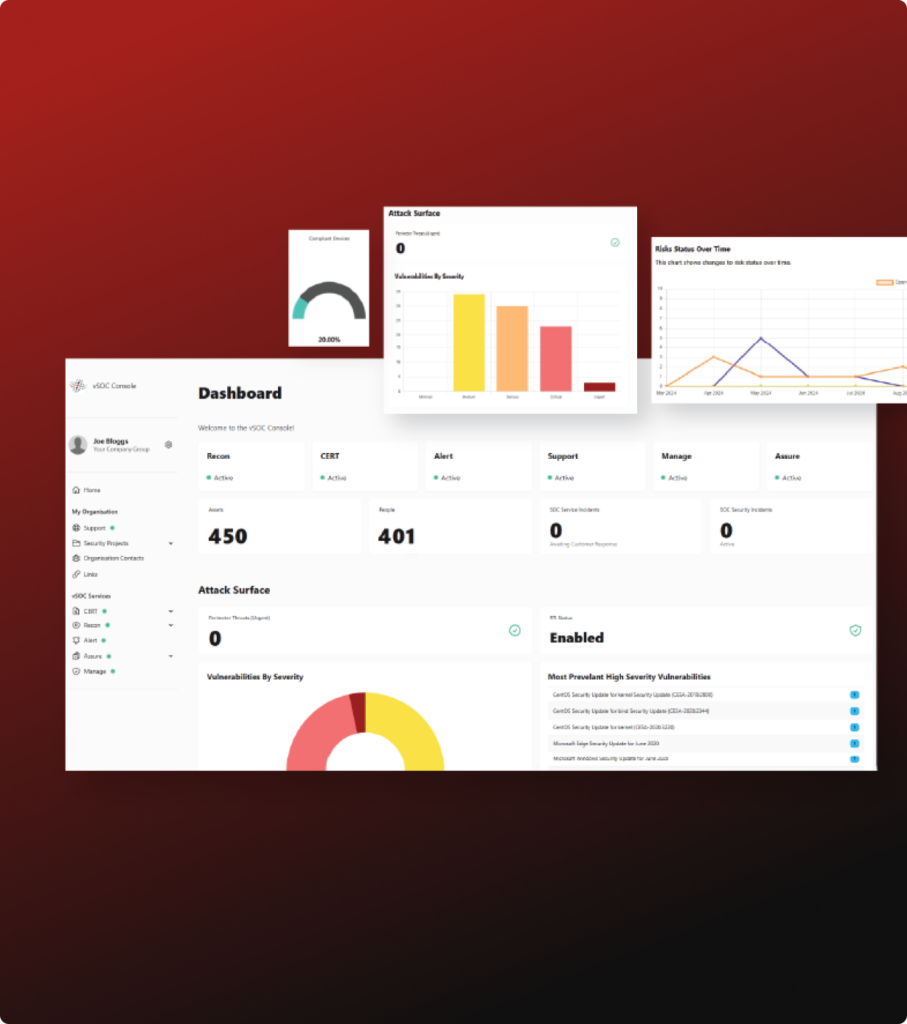
Our Vulnerability Management service helps you continuously monitor, assess and reduce risk across your entire IT environment. Delivered by our expert SOC team and powered by cutting-edge technology, vSOC Recon provides a centralised view of vulnerabilities across your network, devices, applications and cloud environments, all from the intuitive and highly customisable vSOC Connect Console.